DataMiner Cube freeze on startup
Affected versions
All versions of the DataMiner Cube desktop application (DataMinerCube.exe).
Issue description
On a machine without internet connectivity, the DataMiner Cube desktop application will freeze for 20 seconds on startup. Once you have logged in, Cube works fine.
When you go to the file properties of DataMinerCube.exe > Digital Signatures > Details, the same freeze occurs. After 20 seconds, the Digital Signature Details window is displayed.
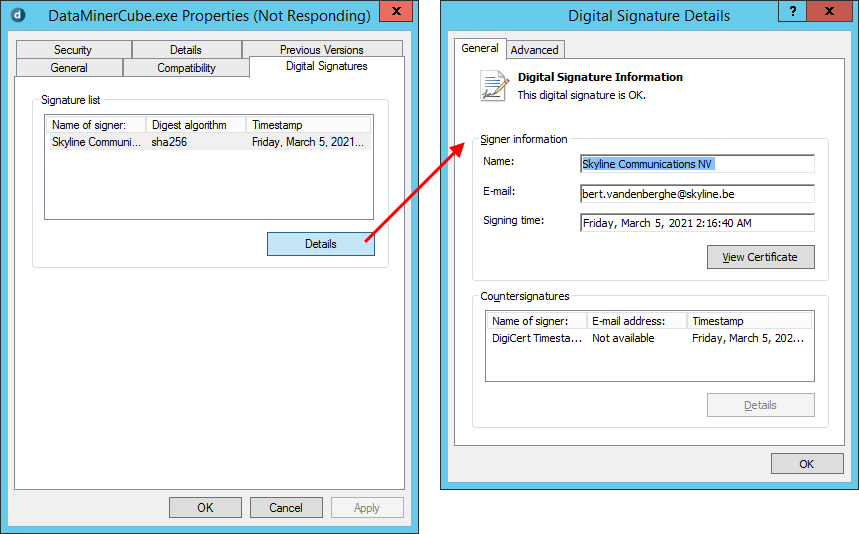
Root cause
.NET Framework/Windows attempts to check the Certificate Revocation List (CRL) associated with the certificate that Skyline uses to sign its applications.
For binaries signed before 2021-07-01, this is with a certificate from COMODO that will attempt to access the following URLs:
For binaries signed after 2021-07-01, this is with a certificate from Sectigo that will attempt to access the following URLs as well:
Terminology:
- CRL: Certificate Revocation List
- CTL: Certificate Trust List
- OCSP: Online Certificate Status Protocol
Background articles:
Workarounds
Compliance – ensure Windows can correctly check the CRL
- Allow Windows to periodically update all CTLs through Windows Update. This requires HTTP access to ctldl.windowsupdate.com.
- Allow Windows to periodically update these specific CRLs. This requires HTTP access to the 4 hostnames listed above in the Root cause section.
- Manage the periodic delivery of CTLs to disconnected client machines through any other mechanism.
Avoidance – prevent Windows from checking the CRL
Instruct .NET Framework to not check the CRL for this application (see Microsoft documentation). Place a file named DataMinerCube.exe.config alongside DataMinerCube.exe with the following content:
<configuration> <runtime> <generatePublisherEvidence enabled="false"/> </runtime> </configuration>Note
This workaround will be applied automatically when Cube is deployed via the launcher MSI.
Instruct Windows to not check the CRL for any application, by disabling the setting Internet Options > Advanced > Security > Check for publisher's certificate revocation.
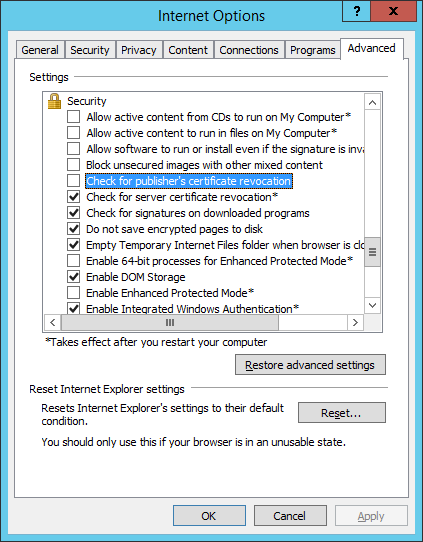
This setting can also be disabled via its registry key:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\WinTrust\Trust Providers\Software PublishingSet value State to
146944(decimal) or0x00023e00(hex).Note
There is no built-in group policy available in Windows for this setting.
Mitigation – allow Windows to attempt to check the CRL, but ensure this attempt fails quickly instead of waiting for a timeout
On the local machine: Redirect the affected hostnames in the
C:\Windows\system32\drivers\etc\hostsfile.127.0.0.1 ocsp.comodoca.com 127.0.0.1 crl.comodoca.com 127.0.0.1 ocsp.sectigo.com 127.0.0.1 crl.sectigo.comOn the network firewall: Do not silently drop packets to these hostnames on TCP port 80. Instead, reject the connection so the client is immediately informed that no connection can be made and does not wait for a timeout.